Introducing zPassport

Introduction
From KYC/AML checks on Coinbase to age verification on Instagram, platforms are increasingly demanding proof of identity to gain access to their services. Unfortunately, these same platforms often prefer to collect excessive amounts of personally identifiable information (PII) rather than risk failing regulatory compliance. Authentication often requires a combination of PII, such as:
- Identity Documents: Passports, driver's licenses, Social Security numbers
- Financial Records: Bank statements, tax documents, bills
- Biometric Data: Facial scans, voiceprints, fingerprints
These authentication requirements are often paired alongside vague promises such as: "Your ID will be stored securely on our servers and is deleted within 30 days.”
With no clear information on how this data is used and no way for users to enforce exactly what is stored, the security and privacy-preservation of these centralized identity verification systems can be reduced to a single phrase: "Just trust us."
We can do better.
Today, I’m introducing zPassport, a decentralized and privacy-preserving service for generating verifiable digital credentials. Through zPassport, users will be able to definitively prove properties about their identity online while maintaining full control over exactly how much information is revealed.
What is zPassport?
Built on zero-knowledge cryptography and the Aleo blockchain, the zPass model enables private identity verification without revealing the underlying data. Instead of showing your full passport or driver’s license to prove your age or nationality, zPass lets you prove just the fact that you meet the requirement—and nothing more. It’s a powerful shift toward user-controlled digital identity that preserves both security and privacy.
zPassport is taking this concept one step further: using official digital passport data as the foundation for issuing zPass credentials. This approach builds directly on the existing infrastructure of trusted government-issued documents, transforming them into verifiable digital credentials. The result is a secure, interoperable bridge between real-world identity and privacy-preserving, verifiable digital identity, unlocking a future where proving who you are no longer means giving everything away.
Background
Passports
If you have a traditional passport and look at the front cover, chances are you’ll see this symbol:
This means that your passport has an embedded RFID chip which contains a digitized version of all the critical information stored. This technology is commonly referred to as a biometric passport, or e-passport. The information is encrypted, with the key to decrypt it being listed in the machine-readable zone (MRZ) at the bottom of the ID page of the passport.

In addition, a digital signature is included alongside the information on the chip. This digital signature is derived from the issuing country's security certificates—the Country Signing Certification Authority (CSCA) Certificate and the Document Signer Certificate (DSC). Together, the signature and certificates form a trust chain wherein one end is securely anchored in the authority of the issuing country and the other end is securely stored in the chip of the ePassport as the Document Security Object.
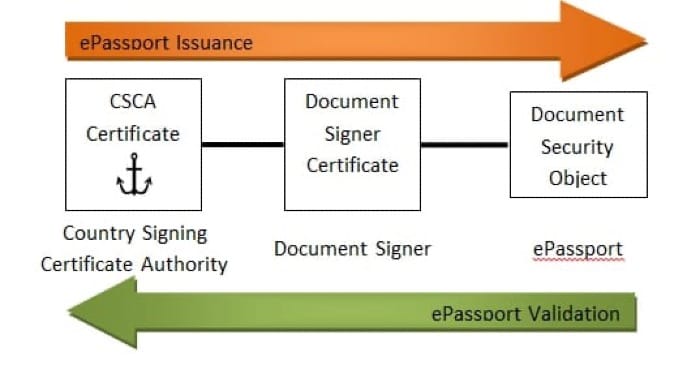
The critical features of this technology that make zPassport possible are:
- Every digital signature can be verified using the respective certificates, which are made publicly available by the issuing country.
- The embedded microchip can be read by any compatible RFID/NFC scanner, including most modern mobile phones (this is the same technology that makes things like Apple Pay work).
Aleo and Zero-Knowledge Proofs
A zero-knowledge proof (ZKP) is a cryptographic technique that lets one party prove to another that a statement is true—without revealing any of the underlying information that makes it true. For example, you could prove that you're over 18 without revealing your exact birthdate or identity. Aleo is a decentralized blockchain built specifically to support private applications using zero-knowledge proofs. It allows developers to create apps where users can compute and verify data off-chain (i.e. privately), while posting checkable, encrypted proofs—not the data itself—to the blockchain. This means Aleo combines the trust and transparency of blockchain with the privacy of zero-knowledge cryptography, enabling a new generation of apps—like zPassport—that are both decentralized and privacy-preserving.
How does zPassport work?
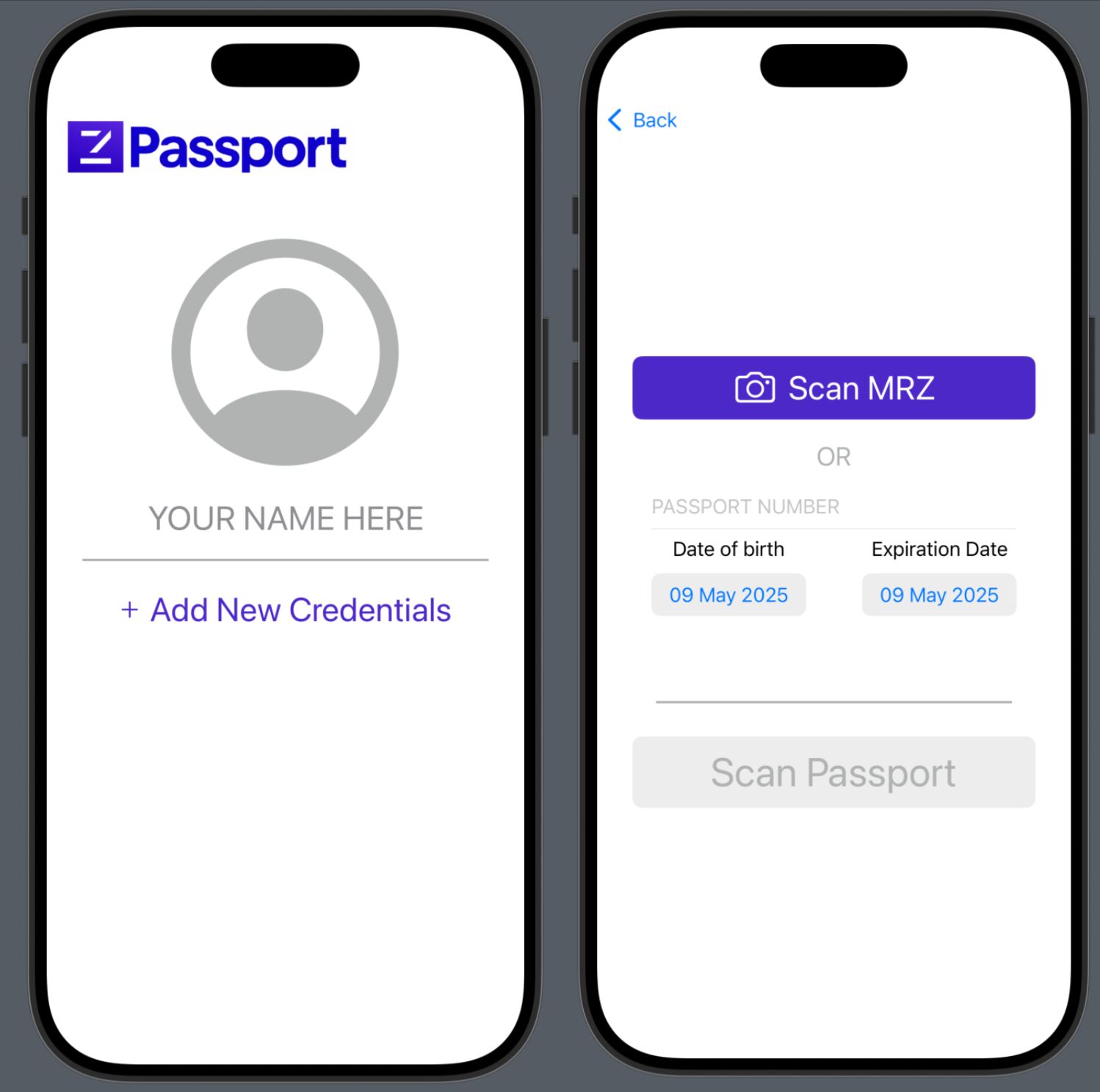
The procedure is simple in principle: users should be able to digitally scan their passport, produce some verifiable, unforgeable credentials on their device, and then use those credentials to perform privacy-preserving identity checks with 3rd party services.
Generating Credentials
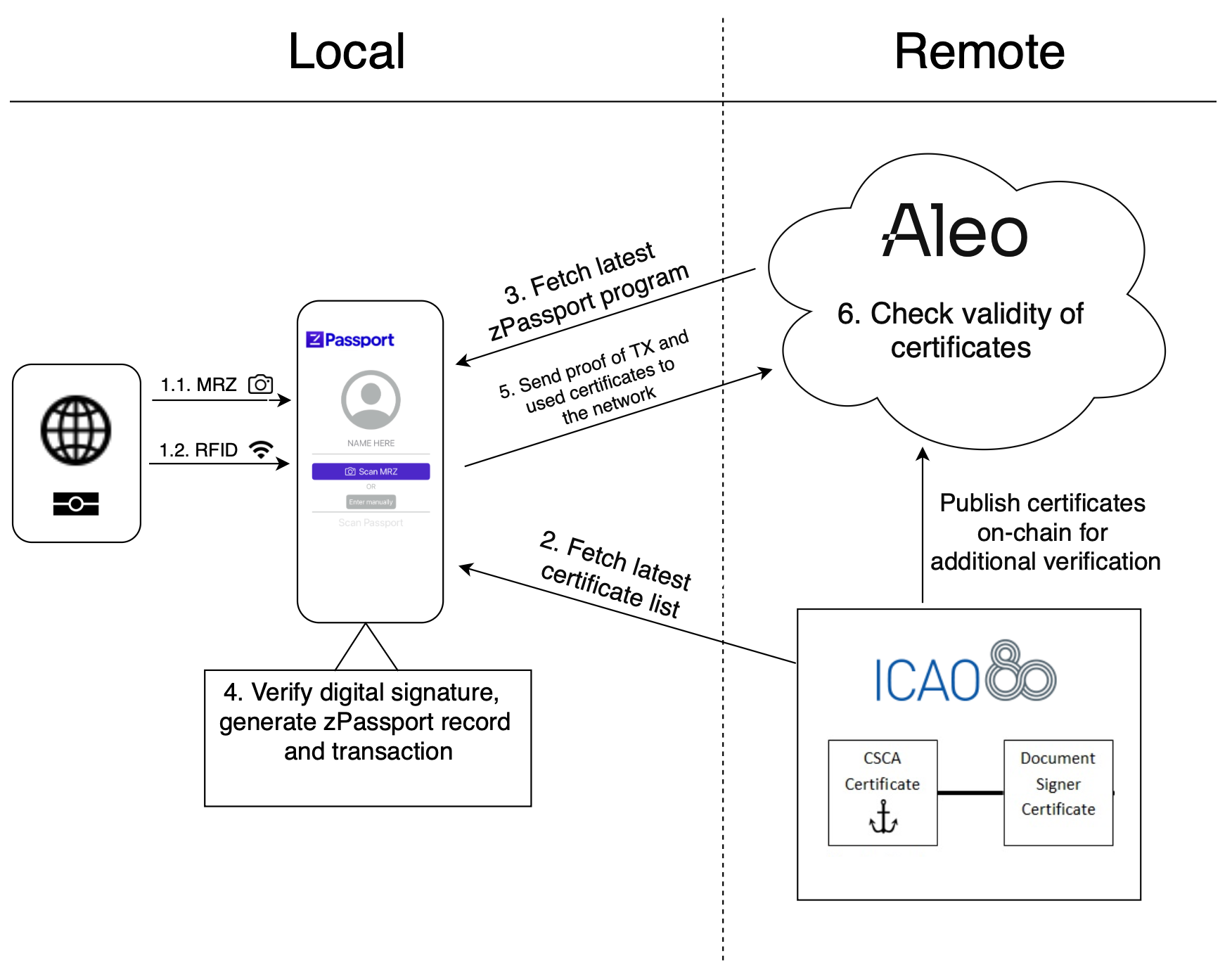
Workflow
- Users scan the MRZ on their passport using the device's camera. The decryption key is parsed from the image using an optical character recognition (OCR) model. Using the mobile device's built-in RFID/NFC scanner, the encrypted passport data is read and decrypted using the parsed key.
- The latest official national certificates list is fetched from a trusted authority. These certificates are published by various state entities and international organizations, but the most accurate and comprehensive comes from the International Civil Aviation Organization (ICAO), a United Nations agency that maintains the international passport standard.
- The latest version of the
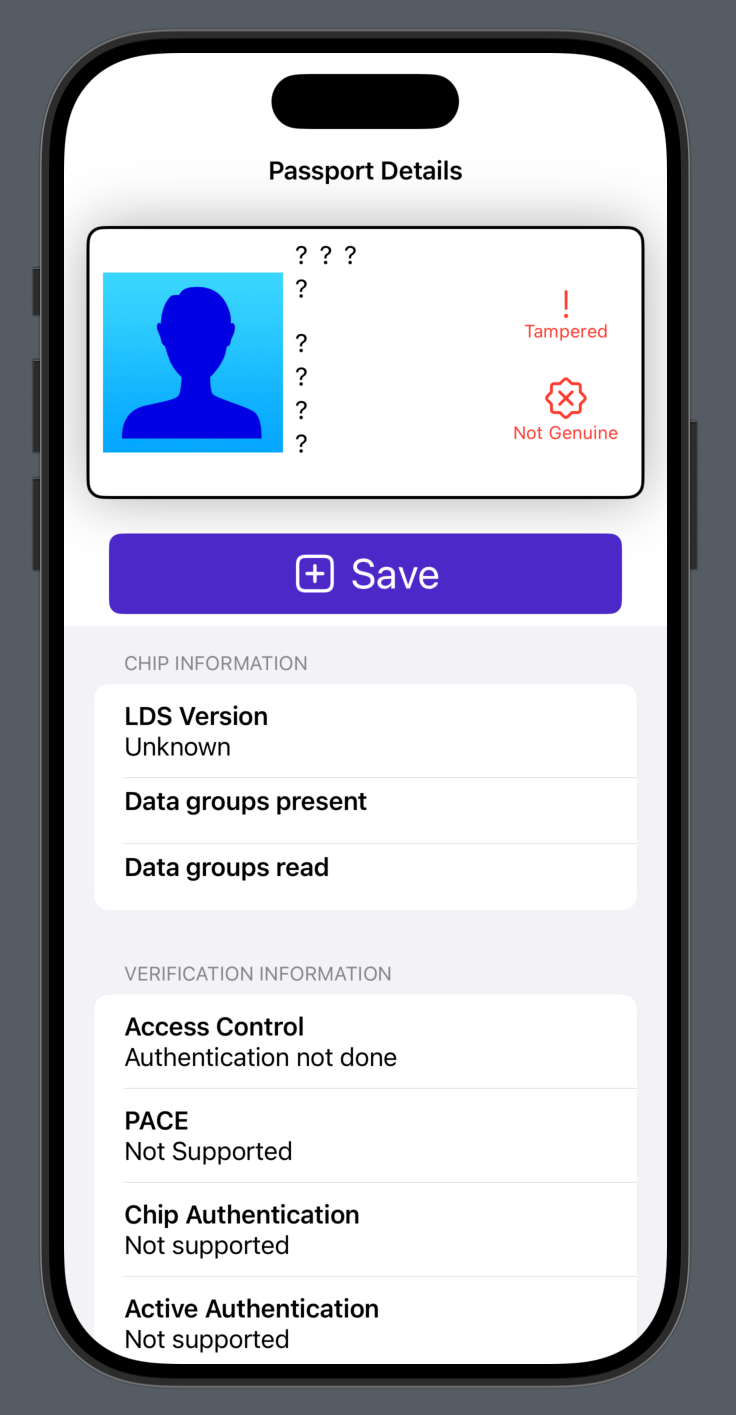
zPassport.aleoprogram is fetched from the network. - On the local device, the passport data is checked for correct formatting, and the certificate trust chain is verified. The signature verification is typically a combination of one of the SHA-2 family of hashing algorithms and either ECDSA or RSA. Once the data and signatures have been verified, the
issue_credentialfunction is executed locally. This function takes as input the fundamental passport data (name, passport number, date of birth, date of expiry, etc.), the digital signature, the hash of the passport data, and the certificates that will verify the signature. The function will re-run the signature validation against the provided hash in Leo (the domain-specific language of Aleo) for redundancy. Upon success, the function will produce an encrypted record corresponding to the newly minted passport credential, as well as a transaction that contains a zero-knowledge proof of execution. - The transaction is broadcast to the network, alongside instructions to execute the corresponding on-chain counterpart function for
issue_credential. - The on-chain function checks the provided certificates against the official on-chain registry. If this check passes, then the transaction is accepted by the network, and the credential minted off-chain is considered valid. If this check fails, then the entire transaction (including the produced passport credential) is considered invalid.
User privacy is never compromised, because the only information revealed to the network is:
- The encrypted passport data, stored as an encrypted Aleo
Record, which can only be decrypted by the owner - The zero-knowledge proof of execution validity
- The country security certificates used
Verifying Credentials
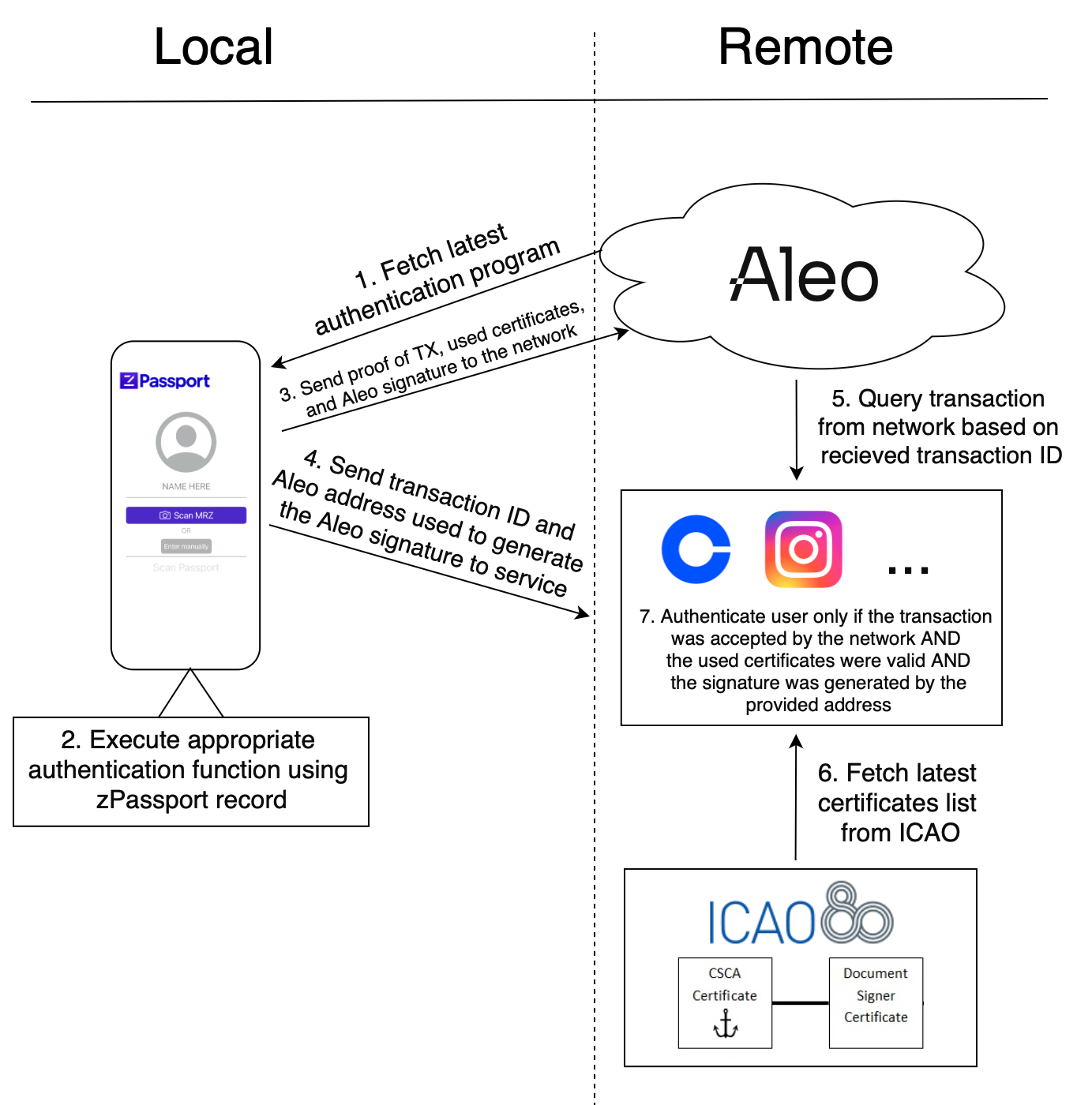
Workflow
- The latest version of the desired authentication program is fetched from the Aleo network.
- Using the locally stored zPassport credential as input, the appropriate function is executed. For example, one might wish to prove that they are above the age of 18, so they would execute the function that checks that the
ageparameter of the zPassport record is greater than or equal to 18. Upon success, the function will produce a new version of the zPassport record (as records in Aleo can only be consumed once), as well as a transaction that contains a zero-knowledge proof of execution. - The transaction is broadcast to the network, alongside instructions to execute the corresponding on-chain counterpart function, the used certificates, and an Aleo signature from the user's Aleo address.
- Upon the transaction being successfully processed by the network, the user then sends the transaction ID along with the Aleo address used to generate the Aleo signature directly to the service.
- The service queries the Aleo network for the transaction ID provided by the user.
- The service also queries the latest certificates list from a trusted source (ICAO, US State Department, etc.).
- The user will be succesfully authenticated only if the transaction was successful AND the certificates used in the transaction match the ones retrieved from the trusted entity AND the Aleo signature from the transaction was produced by the Aleo address sent by the user directly.
Once again, user privacy is never compromised, because the only information revealed to the service is:
- The encrypted passport data, stored as an encrypted Aleo
Record, which can only be decrypted by the owner - The zero-knowledge proof of execution validity
- The country security certificates used
- The Aleo address used to generate the signature, which in practice can be a one-time usage address
App Prototype
Limitations
Despite the conceptual benefits of zPassport, there are several limitations that currently prevent it’s functional implementation.
RSA/ECDSA
As mentioned earlier, the signature verification process is typically a combination of one of the SHA family of hashing algorithms and either ECDSA or RSA.
Unfortunately, there is no native support for the previous generation of SHA hashing algorithms or RSA/ECDSA signature verification on Aleo. This is due to the fact that RSA typically uses modulus values of the order of 2048-bits, which is significantly larger than the largest supported values. ECDSA, on the other hand, typically uses a different set of elliptic curves than the ones supported on Aleo.
For RSA, this problem will be easily fixed in the coming weeks/months once writable arrays come to Leo. There is a clever way to compute modular arithmetic for arbitrarily large values using bit-shifting, but it unfortunately requires arrays to be modifiable.
For ECDSA and implementing the legacy SHA algorithms, the path forward is less clear, though I believe that adding support at a core network architecture level would improve interoperability with both traditional Web2 data as well as other chains.
On-chain Certificate Registry
Access to the latest CSCA and DSC certificates on-chain will require either a trusted entity such as ICAO to officially publish them or, more likely, an oracle service to bridge this data from the ICAO website to the Aleo blockchain. The oracle model is well-established throughout web3, and several projects on Aleo are actively developing oracle services as a way to bridge various legacy data to the on-chain ecosystem.
Credential Duplication
There needs to be a way to prevent the same credential from being minted multiple times, either by the same user or in the event a physical document is stolen or lost. This can be accomplished by extending the issue_credential program to compute a cryptographic commitment to a given set of passport data, then storing a mapping of those commitments on-chain. The official zPass documents have a great example of this in practice.
Summary
zPassport offers a bold vision for the future of digital identity—one that honors both security and personal agency. By leveraging trusted passport infrastructure, modern cryptography, and Aleo’s privacy-preserving blockchain, zPassport creates a seamless bridge between real-world identity and private digital verification. Users can now prove exactly what’s needed—no more, no less—without ever surrendering control of their personal data to centralized platforms. While there are technical challenges ahead, the path forward is clear: zero-knowledge identity systems like zPassport are not just possible—they’re necessary.
